
Gary Gensler’s Securities and Exchange Commission (SEC) has striven to be tough on the bad actors of the online world. Now, the SEC is enacting tough new measures to combat cyberattacks.
Under the new rules, registrants will have to be more forthcoming about cyber breaches they undergo. They will face stiffer reporting requirements. Including yearly disclosures to the SEC about the systems and protocols they have in place to thwart breaches. There can be no doubt of the severity of cybersecurity vulnerabilities. Yet some may still question the SEC’s priorities.
SEC Reporting Requirements Are Strict
Gensler’s regulators mean business and have codified the new policy with a written requirement. When registrants fill out Form 8-K, they will find a new item, 1.05. There they will have to provide details of any cyber incident with what the agency would consider a “material impact.”
The form will require information on “the material aspects of the incident’s nature, scope, and timing, as well as its material impact or reasonably likely material impact on the registrant,” according to the SEC’s announcement.
Registrants will have four days after the incident to provide a 1.05 filing with the requested information. Although the SEC may allow more time when disclosure could have national security implications.
Put simply, the rules of the road are different now. You cannot suffer a breach of your cyber defenses and carry on as if nothing happened that might be of concern to regulators or to your investors.
Regulation S-K Item 106 imposes further requirements. Firms and exchanges will have to provide a lot of data on the systems they have in place to spot and thwart cyber threats. Including their board of directors’ level of attention to the issue.
Annual reports will have to offer all these disclosures on Form 10-K. Foreign private issuers face similar, but separate, disclosure requirements.
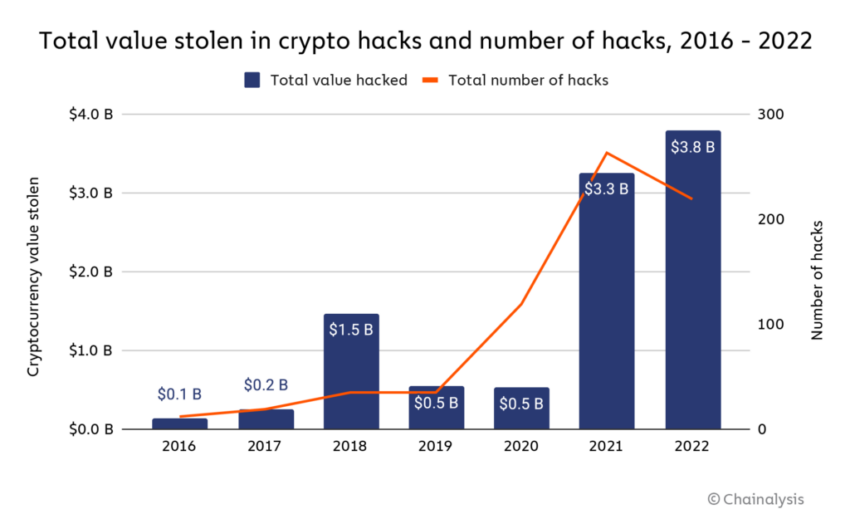
Cyberattacks on the Rise
While the problem that the SEC sets out to address here is real enough, its new rules may give rise to sentiments of “Physician, heal thyself!”
That is to say, cyberattacks don’t just target firms and exchanges. They hit governments hard. Many governments in recent months have done a poor job of erecting firewalls against cyber breaches.
For example, a recent study by cybersecurity firm Surfshark found that more cyberattacks affected government bureaus in the first quarter of 2023 than in all of 2022.
Presenting these findings, Surfshark drew on data from the Center for Strategic and International Studies (CSIS).
US Agencies Suffer Breaches
The CSIS findings are startling. As recently as last month, the Department of Energy and other US federal agencies suffered a severe cyber breach. The bad actors were, allegedly, hackers with ties to Russia.
“Cybercriminals targeted a vulnerability in software that is widely used by the agencies, according to a US cybersecurity agent,” the CSIS report stated.
And, in March 2023, reports emerged that an unnamed US federal agency suffered a breach at the hands of Vietnam-affiliated hackers. The attack was no quick and random incident, but stretched from November 2022 to January 2023. The bad actors reportedly found a gap that enabled them to install malware in the Microsoft server on which the agency relied.
If government agencies are not safe, none of us are. It is well and good for the SEC to make a show of being tough with cryptocurrency and other exchanges. But some may wonder if it is doing so at the expense of ignoring more pressing problems.
Disclaimer
In adherence to the Trust Project guidelines, BeInCrypto is committed to unbiased, transparent reporting. This news article aims to provide accurate, timely information. However, readers are advised to verify facts independently and consult with a professional before making any decisions based on this content.

Leave a Reply